SNMP Protocol | Complete Process, Commands, Attacks and Security
Simple Network Management Protocol [SNMP Protocol(Port 161, 162)]
Introduced in 1988, the Simple Network Management Protocol used to meet the purpose of network and Internet Protocol-based device management and monitoring. SNMP uses UDP port 161 & 162. It aims at providing a common language to all the network devices which helps them to communicate with each other. SNMP helps network devices like router, switches, hub, etc to share information. It also helps in fault detection and configuration of remote devices. SNMP already has 3 versions developed and deployed SNMP v1, SNMP v2 & SNMPv3. V2 and V3 were bug fixed and improved to their original version.
In SNMP, no message encryption takes place and so SNMP protocol is not a secure way of sharing information.
SNMP Protocol works on a client server architecture which consists of three components.
Architecture of SNMP
- Managed Device
- SNMP Agent
- Management Information Base (MIB)
- SNNP Manager
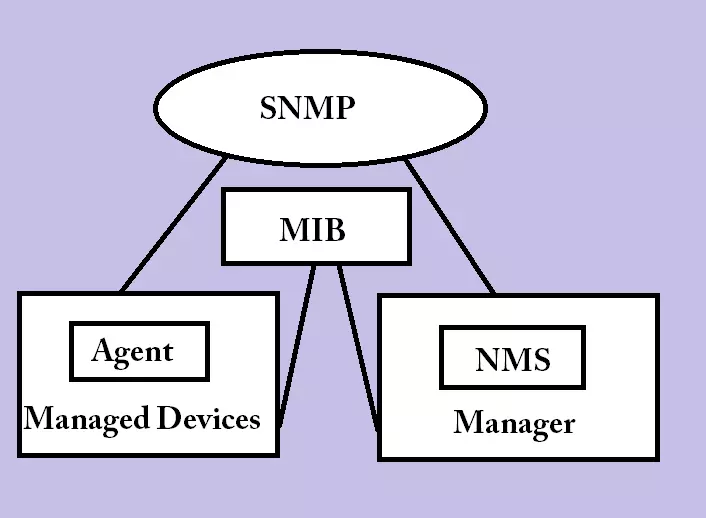
Managed Device
Managed Device refers to the network devices which need to communicate in order to make a particular transaction complete. The communication can be from one side or even both sides.
SNMP Agent
All the network devices like router, switches, etc need some software program installed in it. These software programs collect the required information from the network devices (SNMP enabled only) and provide that information to the database. For example, In the case of routers, data from routing tables get stored to databases from where other routers can match it for further packet transmission.
In case of non-SNMP devices, the agents work as a proxy. In proxies, the conversion of request takes place from one SNMP version to another.
Management Information Base (MIB)
Management Information Base, also called Management Information Database .i.e. the database of all the information and parameters. MIB collects data from agents and maintain it as variables in the form of hierarchies. It stores the variable objects with the values in a text file with uses .mib extension.
SNMP Manager
SNMP manager refers to a centralized network management system (NMS). Usually, SNMP manager means the server hardware and the software installed on it for monitoring and management of network devices refer to the NMS. The MIB collects data/information from agents and shares it with the SNMP manager. The process of information sharing and collection repeats after regular intervals.
SNMP Working Process
- SNMP Protocol uses UDP port at the Transport layer.
- NMS software on the manager request for the data in the form of variables via any port.
- The agent receives the request at port number 161 and sends the response back to manager via source port.
- Now agent sends the notification message packets to the manager on port number 162.
All these requests and responses travel in the form of unit known as Protocol Data Units (PDU). SNMP mainly uses the following PDU messages:
- GetRequest: A request sent by the manager to the agent asking for the current values or variables or a list of variables.
- GetNextRequest: A (similar to GetRequest) request to get the value of next variable.
- SetRequest: A request made by the manager in order to modify the value or list of variables.
- Response: The response given by the agent as an acknowledgment to the manager.
- Trap: The agent sends the trap to notify about the occurrence of events.
- InformRequest: Came into action with v2 SNMP where the idea of the manager giving a confirmation after receiving the response got introduced.
Example
In this example, we used get command with sysName.0 to get the admin assigned name for the agent node.
snmpget -mALL -v1 -cpublic snmp_agent_Ip_address sysName.0 SNMPv2-MIB::sysName.0 = STRING: KHUSHANKBHAGWAN PC
Difference between SNMP versions v1, v2, v3
SNMP v1
- The first and original version of SNMP.
- Criticised for security as no authentication mechanism exist. Due to this, it identifies all messages as authentic.
- Security was highly dependent on channel.
- No encryption mechanism causing the clear text transmission.
SNMP v2
- No major changes introduced. Only a few improvements implemented.
- It can also be configured over UDP.
- New PDU named GetbulkRequest introduced. It can be used to get huge data at one go. Also SNMP Proxy came as a new feature..
- Upgrade of 32-bit counters to 64-bit counters. It can store up to 18.4 quintillion values.
SNMP v3
- Improved authentication mechanism with the use of Hash based MAC with SHA or MD5.
- Privacy protected with a 56-bit DES encryption algorithm.
- SNMP entity identifier came into existence.
- As of now, SNMP v3 is most secure version of SNMPs.
Attacks and Security of SNMP Protocol
- Plain Text Transmission: Since the first two versions don’t use any encryption algorithm. The Password submitted in Cleartext transmission can easily be captured. To avoid sniffing attacks, version 3 should be used.
- Default Strings: The default strings makes it easy for anyone to gain access. and to prevent unauthorized access, default settings must be changed.
- Exposures due to scan: SNMP when enabled uses CPU and network bandwidth. Also, networks can be exposed as SNMP enables network scanning via various software & tools. To prevent this issue, SNMP should be disabled when not in use.
- Brute force and Dictionary attack: Dictionary attack or brute force can crack the passwords since the DES encryption uses only a 56-bit key.
Check out how the SMTP protocol works, It will help you to understand about email and the attacks associated with it here

